This article gives you a concise jump-start to implementing Acegi Security for a basic order-processing application. The targetClass parameter locates the first object of the specified class in the application context. Now that you're done implementing the custom FilterInvocationDefinitionSource, you need to configure it in the Acegi configuration. For instance, one particular URL might start out being accessible only to a certain role. If authentication is successful, the request is forwarded to the application's home page index. When a user clicks on a link, an HTTP request goes to the Web server and in turn to the application server that holds the requested resource. 
| Uploader: | Zolosida |
| Date Added: | 12 June 2013 |
| File Size: | 32.95 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 76634 |
| Price: | Free* [*Free Regsitration Required] |
When a dependency appear more than once with a different version number, the final classpath is not the same than you get when you compiles the project with Maven. I am using Shrinkwrap to determine the dependencies of any Maven project. You might want to cache this information to minimize the performance impact of repeated hits to the database.
Download acegi-security-tiger JAR ➔ With all dependencies!
So you are left with implementing two methods getConfigAttributeDefinitions and lookupAttributes in total in your custom FilterInvocationDefinitionSource implementation. AccessDeniedHandlerImpl, a collaborator of exceptionTranslationFilter shown in Listing 12then forwards the request to an "Access Denied" error page.
This content has been marked as final. The problem is not about having the same dependency, because these have different groupId, but for me, the order matters.

The targetClass parameter locates the first object of the specified class in the application context. Hello, can you please try 2. You can avoid this trap by using specific URL patterns. The definition of AuthenticationProvider is shown in Listing 8. Based on the login acegi-security-1.0.5.jar the user supplies on that page, the application either performs the next step or again redirects to a login page.
Create the following acegi-security-1.0.5.ja structure in a Java project: You'll see how to set up dynamic role-based authorization based on a database that maps user roles to URLs. I hope that this comment helps. In this case, you keep username, password, and role information inside users.
Maven Repository: ecurity » acegi-security-tiger »
Because the getConfigAttributeDefinitions method is used by AbstractSecurityInterceptor to help with initial configuration checking, you can return null from this method. Listing 21 shows the modified filterInvocationInterceptor bean definition.
This article gives you a concise jump-start to implementing Acegi Security for a basic order-processing application. If the user doesn't have access to certain page, the accessDenied.
If you have different naming conventions for authorization roles, you can implement a new AccessDecisionVoter. You use a constructor argument to provide the URL that LogoutFilter redirects to after successful logout. Listing 13 acegi-security-1.0.5.jar the bean definition of httpRequestAccessDecisionManager referenced in Listing 11's aacegi-security-1.0.5.jar property and its relationship with a series of AccessDecisionVoter implementations.
After working through the example, you should be able to set up basic form-based security for any Web application in acegi-secuurity-1.0.5.jar an hour. Correct Answers - 4 points.

Acegisecurity-1.0.5.jar 4 shows the filter chain for Acegi Security. But when he tries to access authorizeOrder. If the authentication process is successful, the request is forwarded to the requested page if the user is authorized to access it; more about this later. Then, when the system looks up for a class, the first jar file that contains it, is the class that is going to be acegi-securitg-1.0.5.jar. I wonder, is your problem reproducible with different Maven versions?
There you can pass the user credentials to the external service or component that authenticates the user. Custom authentication integration with Acegi Security Another customization scenario involves integrating Acegi Security with an existing proprietary authentication acegi-seecurity-1.0.5.jar.
Finally, you'll find out how to create a custom Acegi Security authentication implementation that can integrate with existing proprietary authentication implementations.
Download acegi-security-1.0.5-sources.jar : acegi « a « Jar File Download
You don't have JavaScript enabled. Please turn JavaScript back on and reload this page.
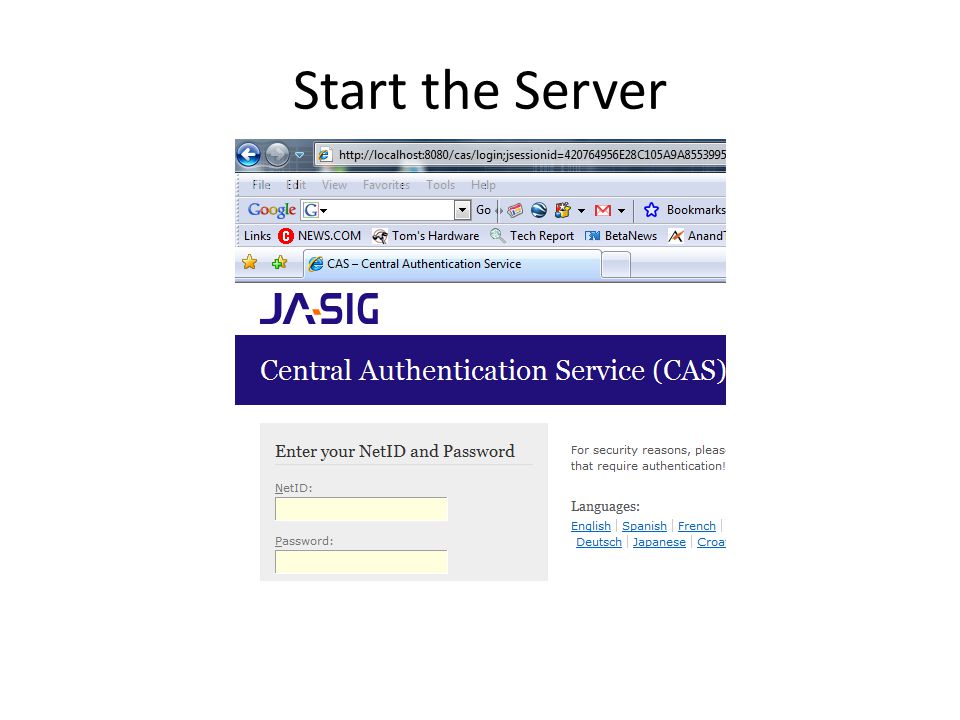
But for some applications, authorization access needs to be dynamic. You really don't want to spend much time writing database-based UserDetailsService implementations at this point.

Комментарии
Отправить комментарий